Cyber Security Invloves securing multiple aspect of business which includes application, data, network and physical devices. Today we will explore the Network part of Cyber security and will discuss Zero Trust Principle in great detail.
What is Cyber Security?
Cybersecurity involves protecting computer systems, networks, and data from unauthorised access and cyber attacks.In today’s digital age, cybersecurity is crucial for safeguarding sensitive information and ensuring business continuity.The cyber threat landscape is diverse, encompassing malware, phishing, ransomware, DoS attacks, and insider threats.Common attack vectors include malware infections, deceptive phishing emails, ransomware attacks, insider risks, and social engineering tactics.
Cyber Security can applied to
- Application
- Information
- Network
- Operations
- Encryption
- Access Control
- End User Usability Education
- Diaster Recovery

Top Cyber Security Treats faced by Users
Network Security principles.
Network Security is one of the important aspect of Cyber Security, it allow us to restrict malicious intent actors to access resources of our Network. The are famously 2 principles to Secure our Network.
- Perimeter Security
- Zero Trust Principle
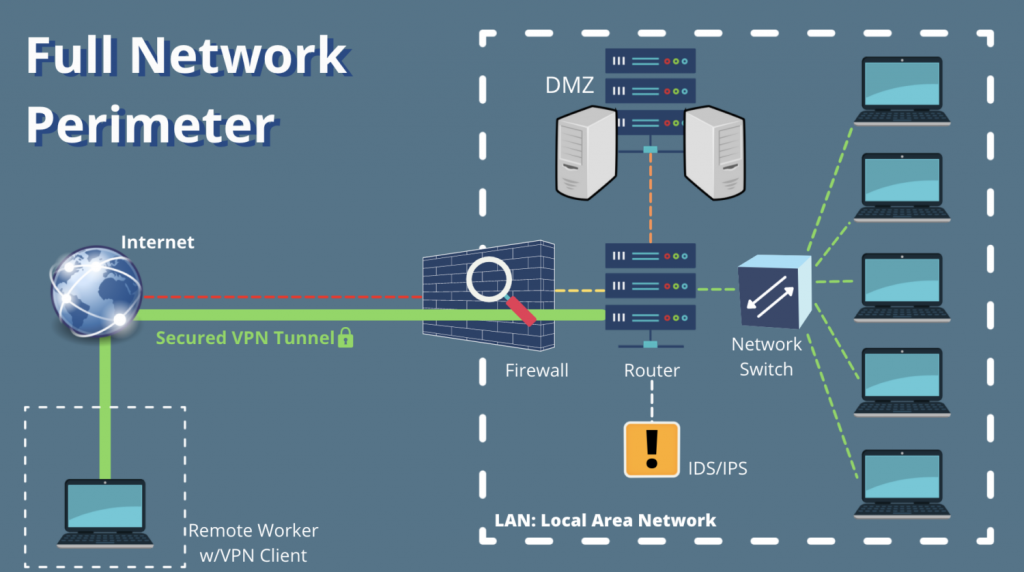
Perimeter Security
Perimeter security refers to the protection of the boundary of a network or system from unauthorized access and external threats. Securing the perimeter is crucial as it acts as the first line of defense against cyber attacks and helps in preventing unauthorized access to sensitive data and resources. This can be achiveved by using following components
- Routers serve as traffic signals for networks directing traffic in and out.
- Firewalls provide a much more thorough check for specific threats.
- Intrusion Detection Systems (IDS) are alarm systems, detecting and warning cybersecurity personnel of any suspicious activity and are built from a single device or a series of sensors within your network at strategic points.
- Intrusion Prevention Systems (IPS) can detect and attempt to automatically defend the system without human intervention.
Limitations of Perimeter Security
- Inability to Protect Against Insider Threats: Perimeter security measures are primarily designed to defend against external threats, leaving organizations vulnerable to attacks initiated by malicious insiders or compromised accounts.
- Challenges in Securing Remote Workers and Mobile Devices: With the rise of remote work and mobile devices, traditional perimeter security solutions struggle to effectively protect endpoints outside the corporate network perimeter.
- Limited Visibility and Control Over Cloud Services: Organizations increasingly rely on cloud services and SaaS applications, which bypass traditional perimeter defenses, leading to gaps in visibility and control over data.
- Difficulty in Detecting Advanced Threats: Advanced threats, such as zero-day exploits and targeted attacks, may evade perimeter defenses, necessitating the use of advanced threat detection and response capabilities.
- Complexity in Managing Multiple Security Tools: Maintaining and coordinating multiple perimeter security tools, such as firewalls, intrusion detection systems (IDS), and antivirus software, can be complex and resource-intensive.
- Impact of Shadow IT and BYOD: Shadow IT (unauthorized use of software and services) and BYOD (bring your own device) initiatives can circumvent perimeter security controls, leading to unmanaged devices and potential security risks.
- Dependency on Network Boundaries: Perimeter security relies on the concept of network boundaries, which may become less defined in modern distributed and hybrid cloud environments, leading to gaps in security coverage.
- Evolving Nature of Cyber Threats: Cyber threats continue to evolve, making it challenging for traditional perimeter security solutions to keep pace with emerging attack techniques and tactics.
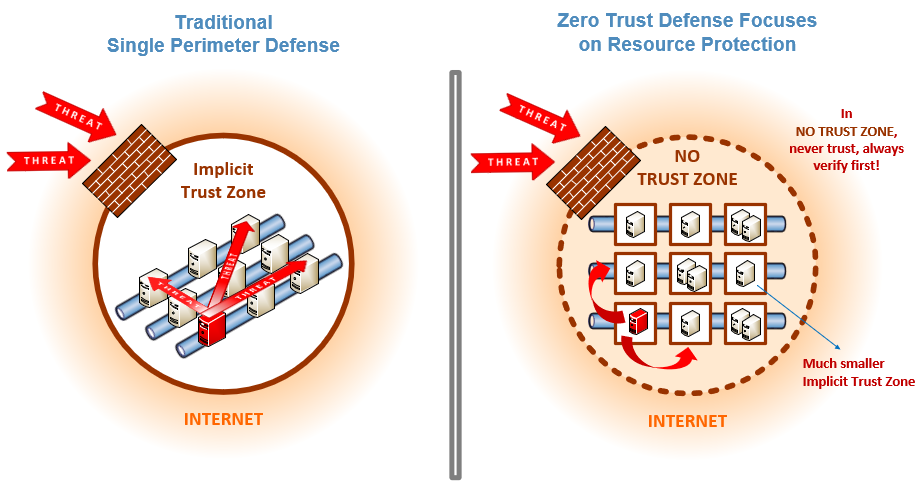
Introduction to Zero Trust
- Zero Trust networking emphasizes the principle of “never trust, always verify,” challenging the traditional perimeter-based security model.
- Throughout this presentation, we have explored the challenges and considerations of transitioning to a Zero Trust security model.
- By adopting Zero Trust principles, organisations can enhance their cybersecurity posture and better defend against evolving threats.
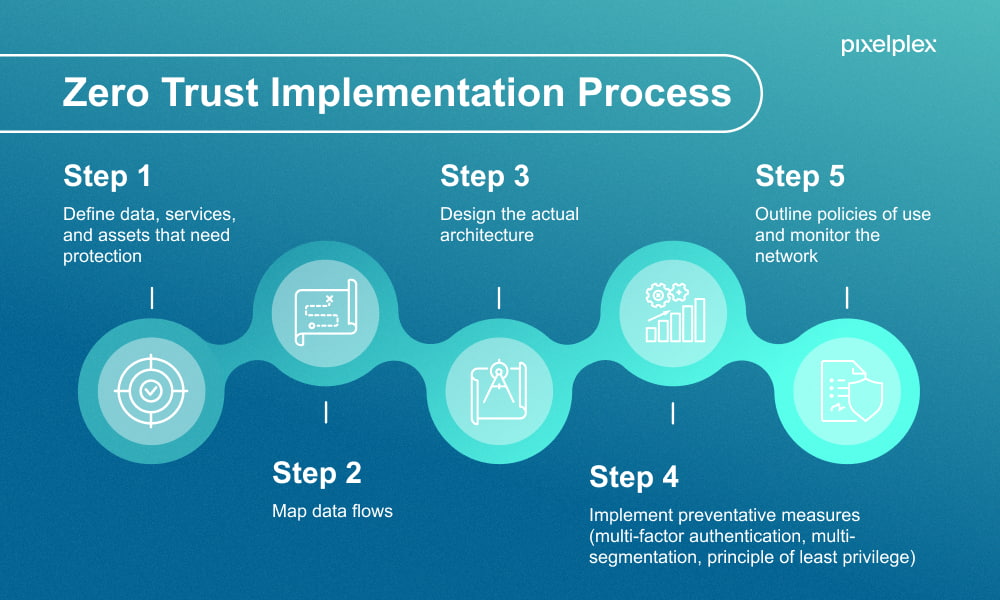
Implementation Strategies
Challenges
- Legacy Infrastructure: One of the primary challenges organizations face when implementing Zero Trust is dealing with legacy infrastructure. Traditional network architectures and security systems may not align with the principles of Zero Trust, requiring organizations to modernize their technology stack and infrastructure.
- Complexity and Integration: Zero Trust implementation often involves deploying multiple security solutions and integrating them seamlessly into existing IT environments. This complexity can pose challenges in terms of configuration, management, and interoperability, particularly for organizations with diverse systems and applications.
- Identity and Access Management (IAM): Effective Zero Trust security relies heavily on robust identity and access management practices. Organizations must accurately authenticate and authorize users, devices, and applications, which can be challenging, especially in dynamic and distributed environments.
- User Experience: Zero Trust implementations should enhance security without compromising user experience or productivity. Balancing stringent security controls with seamless user access and usability presents a significant challenge for organizations, particularly when implementing multifactor authentication and access policies.
- Data Protection and Privacy: Zero Trust focuses on protecting data assets regardless of their location or environment. However, ensuring data privacy and compliance with regulatory requirements, such as GDPR and CCPA, can be complex, especially when dealing with sensitive or regulated data.
Considerations for Successful Zero Trust Implementation:
- Comprehensive Risk Assessment: Before embarking on a Zero Trust initiative, organizations should conduct a comprehensive risk assessment to identify existing vulnerabilities, threats, and security gaps. This assessment helps prioritize security measures and investments based on the organization’s specific risk profile.
- Incremental Deployment: Implementing Zero Trust is a journey rather than a one-time project. Organizations should adopt an incremental approach, starting with pilot projects or specific use cases before scaling across the entire infrastructure. This phased approach allows for testing, refinement, and gradual adoption of Zero Trust principles.
- Collaboration and Alignment: Successful Zero Trust implementation requires collaboration and alignment across various stakeholders, including IT, security, operations, and business units. Establishing clear communication channels, roles, and responsibilities ensures buy-in from all parties and facilitates smoother implementation.
- Automation and Orchestration: Automation plays a crucial role in Zero Trust security by streamlining security operations, enforcing policy enforcement, and responding to threats in real time. Organizations should leverage automation and orchestration tools to automate routine tasks, enhance visibility, and improve incident response capabilities.
- Continuous Monitoring and Adaptation: Zero Trust is not a static security model but a dynamic and evolving approach that requires continuous monitoring and adaptation. Organizations should implement robust monitoring, analytics, and threat intelligence capabilities to detect and respond to emerging threats and security incidents proactively.
