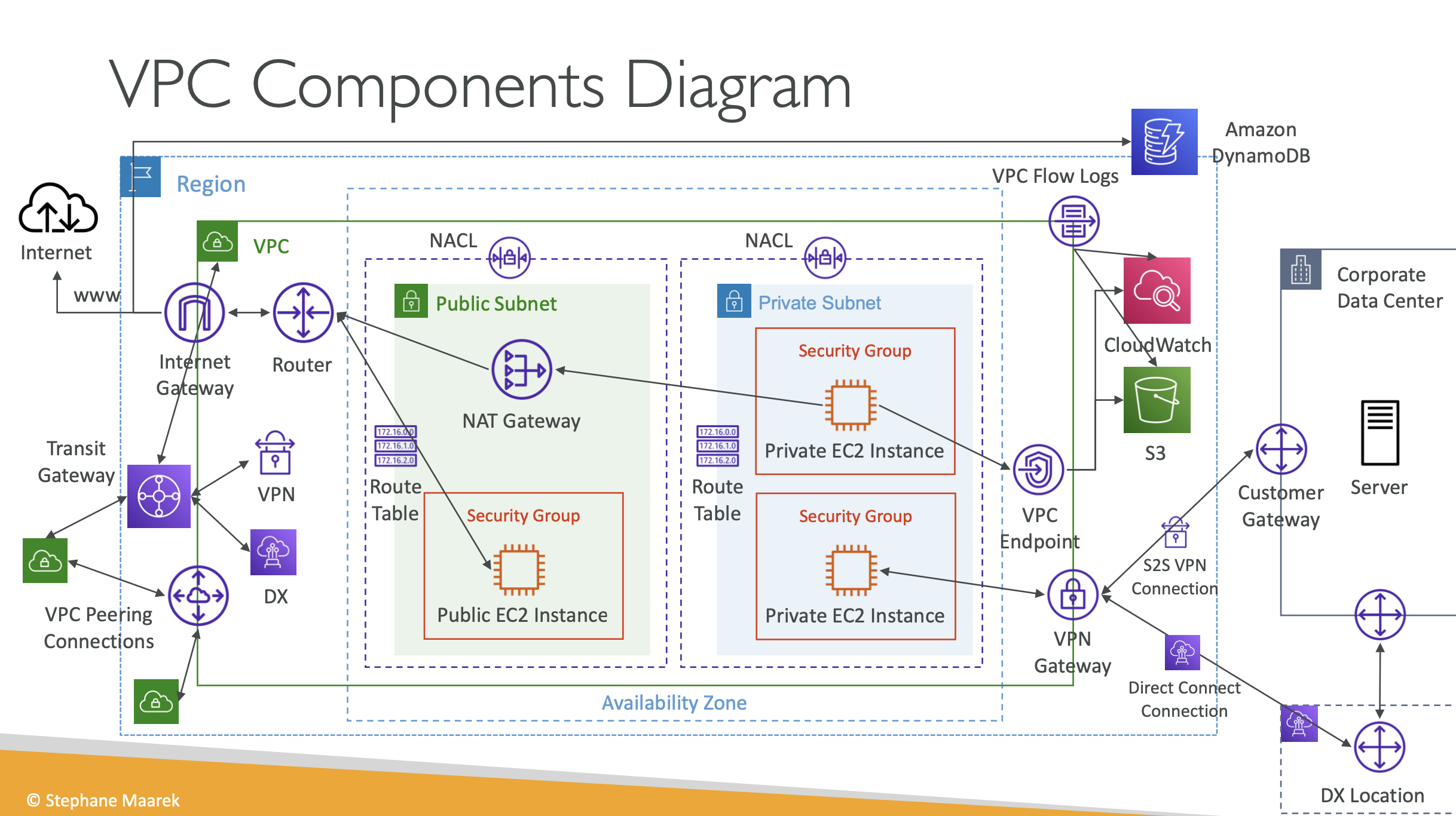
This blog is a part of my journey “Embarking on the AWS Solution Architect Associate SAA-CO3 Certification Journey”
This diagram has all the components that are currently belongs to AWS VPC. If you are able to understand the diagram and know what each components does, congratulations you are well prepared for the AWS Solution Architect Exam
Table of Content
- CIDR -IPv4
- Private IP vs Public IP
- AWS VPC
- Default VPC
- VPC in AWS – IPv4
- Default VPC
- VPC – Subnet (IPv4)
- Internet Gateway (IGW)
- Route Tables
- Different ways to connect to EC2 in private network
- Bastion Hosts
- NAT Instance
- NAT Gateway
- NAT Gateway vs NAT Instance
- Network Access Control List (NACL)
- VPC Peering
- VPC Endpoints (AWS PrivateLink)
- VPC Flow Logs
- AWS Site-to-Site VPN
- Virtual Private Gateway (VGW)
- Customer Gateway (CGW
- Customer Gateway Device.
- AWS VPN CloudHub
- Direct Connect (DX)
- Direct Connect Gateway
- Transit Gateway
- VPC – Traffic Mirroring
- Egress-only Internet Gateway (IPv6)
- Networking Costs in AWS
- AWS Network Firewall
Before diving into AWS VPC, let’s understand a useful concepts like CIDR, Private IP and Public Ip
CIDR -IPv4
- Classless Inter-Domain Routing – a method for allocating IP addresses
- Used in Security Groups rules and AWS networking in general
- They help to define an IP address range:
- We’ve seen WW.XX.YY.ZZ/32 => one IP
- We’ve seen 0.0.0.0/0 => all IPs
- But we can define:192.168.0.0/26 =>192.168.0.0 – 192.168.0.63 (64 IP addresses)
- A CIDR consists of two components
- Base IP
- Represents an IP contained in the range (XX.XX.XX.XX)
- Example:10.0.0.0,192.168.0.0,…
- Subnet Mask
- Defines how many bits can change in the IP
- Example:/0,/24,/32
- Can take two forms:
- /8 -> 255.0.0.0
- /16 -> 255.255.0.0
- /24 -> 255.255.255.0
- The Subnet Mask basically allows part of the underlying IP to get additional next values from the base IP
- 192.168.0.0 / 32 allows for 1 IP (2^0)
- 192.168.0.0 / 31 allows for 2 IP (2^1)
- 192.168.0.0 / 30 allows for 4 IP (2^2)
- 192.168.0.0 / 29 allows for 8 IP (2^3)
- 192.168.0.0 / 28 allows for 16 IP (2^4)
- Base IP
Private IP vs Public IP
- The Internet Assigned Numbers Authority (IANA) established certain blocks of IPv4 addresses for the use of private (LAN) and public (Internet) addresses
- Private IP can only allow certain values:
- 10.0.0.0 – 10.255.255.255 (10.0.0.0/8) (2^24) IPs used in big networks
- 172.16.0.0 – 172.31.255.255 (172.16.0.0/12) AWS default VPC use this
- 192.168.0.0 – 192.168.255.255 (192.168.0.0/16) e.g., home networks
- All the rest of the IP addresses on the Internet are Public
AWS VPC
- Default VPC
- All new AWS accounts have a default VPC
- New EC2 instances are launched into the default VPC if no subnet is specified
- Default VPC has Internet connectivity and all EC2 instances inside it have public IPv4 addresses
- We also get a public and a private IPv4 DNS names
- VPC in AWS – IPv4
- You can have multiple VPCs in an AWS region (max. 5 per region – soft limit)
- Max. CIDR per VPC is 5, for each CIDR:
- Min. size is /28 (16 IP addresses)
- Max. size is /16 (65536 IP addresses)
- Because VPC is private, only the Private IPv4 ranges are allowed:
- 10.0.0.0 – 10.255.255.255 (10.0.0.0/8)
- 172.16.0.0 – 172.31.255.255 (172.16.0.0/12)
- 192.168.0.0 – 192.168.255.255 (192.168.0.0/16)
VPC – Subnet (IPv4)
- AWS reserves 5 IP addresses (first 4 & last 1) in each subnet
- These 5 IP addresses are not available for use and can’t be assigned to an EC2 instance
- Example: if CIDR block 10.0.0.0/24, then reserved IP addresses are:
- 10.0.0.0 – Network Address
- 10.0.0.1 – reserved by AWS for the VPC router
- 10.0.0.2 – reserved by AWS for mapping to Amazon-provided DNS
- 10.0.0.3 – reserved by AWS for future use
- 10.0.0.255 – Network Broadcast Address.AWS does not support broadcast in aVPC, therefore the address is reserved
Internet Gateway (IGW)
- Allows resources (e.g., EC2 instances) in a VPC connect to the Internet
- It scales horizontally and is highly available and redundant
- Must be created separately from a VPC
- One VPC can only be attached to one IGW and vice versa
- Internet Gateways on their own do not allow Internet access.
- Route tables must also be edited! (We will visit Route Table soon)
Route Tables
- A Route Table is a set of rules, called routes, that are used to determine where network traffic is directed within a VPC.
- By default, each VPC comes with a main route table.
- You can also create custom route tables and associate them with specific subnets within your VPC.
- The main route table has a default route that allows outbound traffic to flow to the internet via a VPC’s internet gateway (IGW).
- Custom route tables, on the other hand, don’t have a default route, and you must add routes explicitly.
- A subnet can only have one Route Table
Different ways to connect to EC2 in private network
Bastion Hosts
- We can use a Bastion Host to SSH into our private EC2 instances.
- The bastion is in the public subnet which is then connected to all other private subnets
- Bastion Host security group must allow inbound from the internet on port 22 from restricted CIDR, for example the public CIDR of your corporation.
- Security Group of the EC2 Instances must allow the Security Group of the Bastion Host, or the private IP of the Bastion host
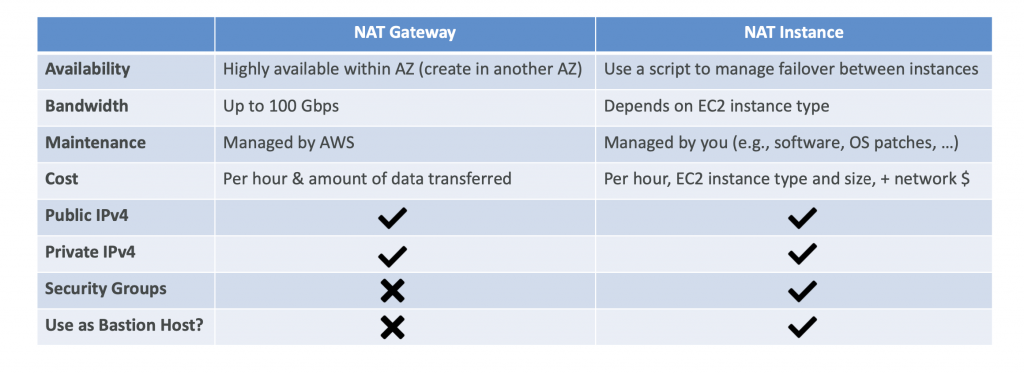
NAT Instance
- An EC2 can be configured to run as NAT Instance.
- We can use Pre-configured Amazon Linux AMI
- Not highly available
- Internet traffic bandwidth depends on EC2 instance type
- Can be used as Bastion Host
- You must manage Security Groups & rules:
- Inbound
- Allow HTTP / HTTPS traffic coming from Private Subnets
- Allow SSH from your home network (access is provided through Internet Gateway)
- Outbound
- Allow HTTP / HTTPS traffic to the Internet
- Inbound
NAT Gateway
- AWS-managed NAT, higher bandwidth, high availability, no administration
- Pay per hour for usage and bandwidth
- NATGW is created in a specific Availability Zone, uses an Elastic IP
- Can’t be used by EC2 instance in the same subnet. *
- Requires an IGW (Private Subnet => NATGW => IGW)
- 5 Gbps of bandwidth with automatic scaling up to 100 Gbps
- No Security Groups to manage / required
- NAT Gateway is resilient within a single Availability Zone
- Must create multiple NAT Gateways in multiple AZs for fault-tolerance
- There is no cross-AZ failover needed because if an AZ goes down it doesn’t need NAT
NAT Gateway vs NAT Instance
Network Access Control List (NACL)
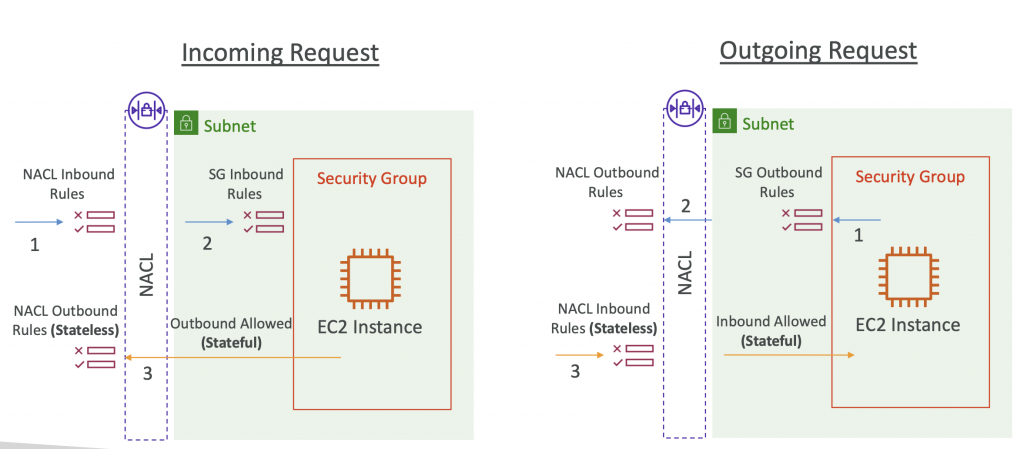
- NACL are like a firewall which control traffic from and to subnets
- One NACL per subnet, new subnets are assigned the Default NACL
- You define NACL Rules:
- Rules have a number (1-32766), higher precedence with a lower number
- First rule match will drive the decision
- Example: if you define #100 ALLOW 10.0.0.10/32 and #200 DENY 10.0.0.10/32, the IP address will be allowed because 100 has a higher precedence over 200
- The last rule is an asterisk (*) and denies a request in case of no rule match
- AWS recommends adding rules by increment of 100
- Newly created NACLs will deny everything.
- NACL are a great way of blocking a specific IP address at the subnet level.
- Default NACL
- Accepts everything inbound/outbound with the subnets it’s associated with
- Do NOT modify the Default NACL, instead create custom NACLs
- Ephemeral Ports
- For any two endpoints to establish a connection, they must use ports
- Clients connect to a defined port, and expect a response on an ephemeral port
- Different Operating Systems use different port ranges, examples:
- IANA & MSWindows10 ->> 49152–65535
- Many Linux Kernels ->> 32768 – 60999
- NACL with Ephemeral Ports
- We need to allow all possible port for connection
- For Example NACL around SQL database should have following rules.
- Allow Inbound TCP On port 3306 From Web Subnet CIDR
- Allow Outbound TCP On port 1024-65535 To Web Subnet CIDR
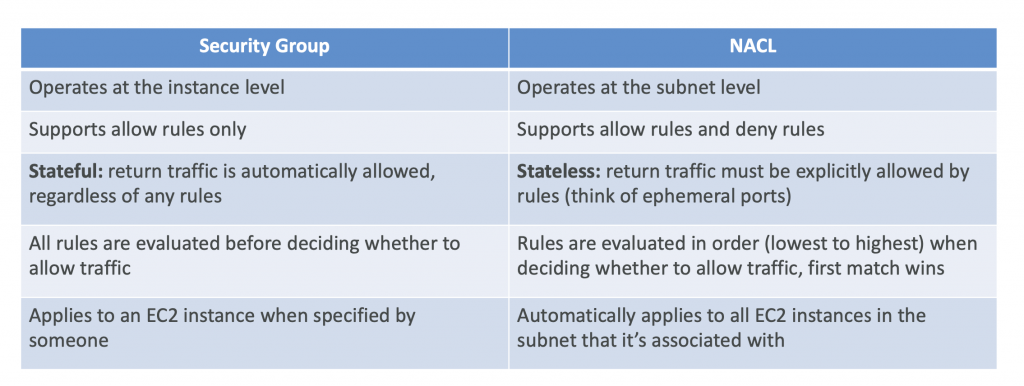
Security Group vs NACLs
VPC Peering
- Privately connect two VPCs using AWS’ network
- Make them behave as if they were in the same network
- Must not have overlapping CIDRs
- VPC Peering connection is NOT transitive (must be established for each VPC that need to communicate with one another)
- You must update route tables in each VPC’s subnets to ensure EC2 instances can communicate with each other.
- You can create VPC Peering connection between VPCs in different
- You can reference a security group in a peeredVPC (works cross accounts – same region)
VPC Endpoints (AWS PrivateLink)
- Every AWS service is publicly exposed (public URL)
- VPC Endpoints (powered by AWS PrivateLink) allows you to connect to AWS services using a private network instead of using the public Internet
- They’re redundant and scale horizontally
- They remove the need of IGW, NATGW, to access AWS Services
- In case of issues
- Check DNS Setting Resolution in your VPC
- Check Route Tables
- Types of Endpoints
- Interface Endpoints
- Provisions an ENI (private IP address) as an entry point (must attach a Security Group)
- Supports most AWS services
- $ per hour + $ per GB of data processed
- Gateway Endpoints
- Provisions a gateway and must be used as a target in a route table (does not use security groups)
- Supports both S3 and DynamoDB
- Free
- Interface Endpoints
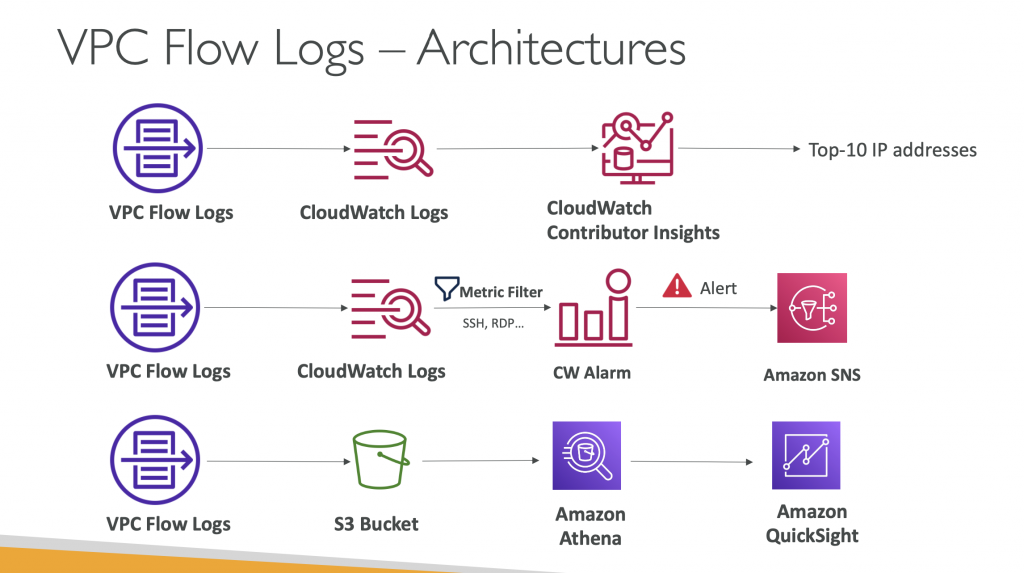
VPC Flow Logs
- Capture information about IP traffic going into your interfaces:
- VPC Flow Logs
- Subnet Flow Logs
- Elastic Network Interface (ENI) Flow Logs
- Helps to monitor & troubleshoot connectivity issues
- Flow logs data can go to S3, CloudWatch Logs, and Kinesis Data Firehose
- Captures network information from AWS managed interfaces too: ELB, RDS, ElastiCache, Redshift,WorkSpaces, NATGW,Transit Gateway
- VPC Flow Logs Syntax
2 123456789010 eni-1235b8ca123456789 172.31.16.139 172.31.16.21 20641 22 6 20 4249 1418530010 1418530070 ACCEPT OK- Version, account-id, interface-id, srcaddr & dstaddr, srcport & dstport, Action
VPC Flow Logs Integration
AWS Site-to-Site VPN
- By default, instances that you launch into an Amazon VPC can’t communicate with your own (remote) network. You can enable access to your remote network from your VPC by creating an AWS Site-to-Site VPN (Site-to-Site VPN) connection
- A Site-to-Site VPN connection consists of the following components:
- Virtual Private Gateway (VGW)
- VPN concentrator on the AWS side of the VPN connection
- VGW is created and attached to the VPC from which you want to create the Site-to-Site VPN connection
- Possibility to customize the ASN (Autonomous System Number)
- Customer Gateway (CGW)
- Software application or physical device on customer side of the VPN connection
- Customer Gateway Device.
- Use Public Internet-routable IP address for your Customer Gateway device
- If it’s behind a NAT device that’s enabled for NAT traversal (NAT-T), use the public IP address of the NAT device
- If you need to ping your EC2 instances from on-premises, make sure you add the ICMP protocol on the inbound of your security groups
AWS VPN CloudHub
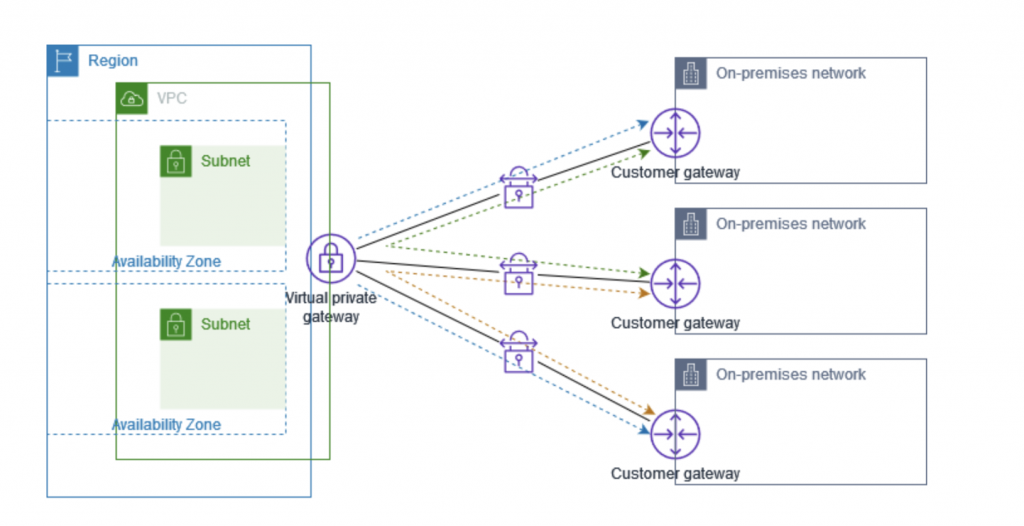
- Provide secure communication between multiple sites, if you have multiple VPN connections.
- Low-cost hub-and-spoke model for primary or secondary network connectivity between different locations (VPN only)
- It’s a VPN connection so it goes over the public Internet
- To set it up, connect multiple VPN connections on the same VGW, setup dynamic routing and configure route tables
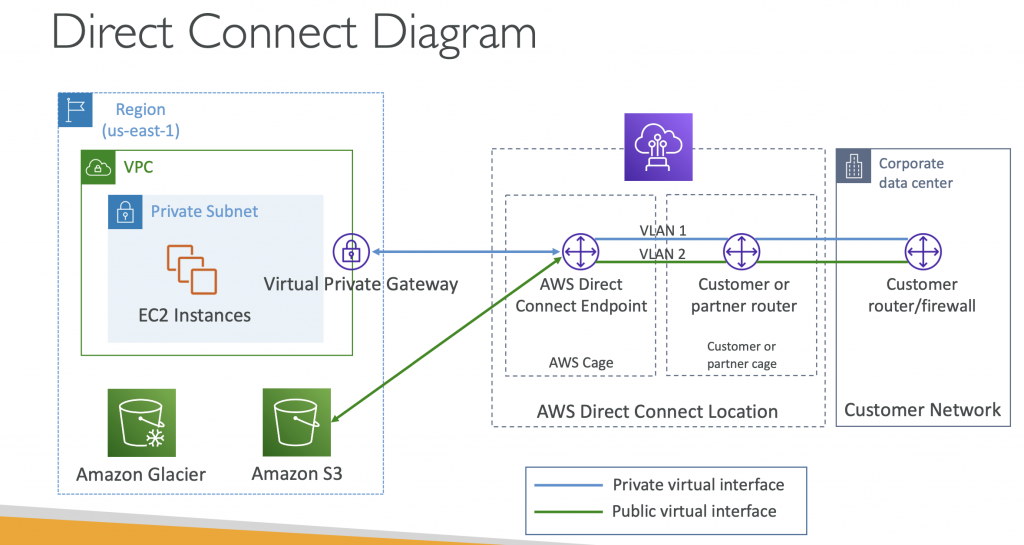
Direct Connect (DX)
- Provides a dedicated private connection from a remote network to your VPC
- Dedicated connection must be setup between your DC and AWS Direct Connect locations
- You need to setup aVirtual Private Gateway on your VPC
- Access public resources (S3) and private (EC2) on same connection
- Use Cases:
- Increase bandwidth throughput – working with large data sets – lower cost
- More consistent network experience – applications using real-time data feeds
- Hybrid Environments (on prem + cloud)
- Supports both IPv4 and IPv6
- Connection Types
- Dedicated Connections: 1Gbps,10 Gbps and 100 Gbps capacity
- Physical ethernet port dedicated to a customer
- Request made to AWS first, then completed by AWS Direct Connect Partners
- Hosted Connections: 50Mbps, 500 Mbps, to 10 Gbps
- Connection requests are made via AWS Direct Connect Partners
- Capacity can be added or removed on demand
- 1, 2, 5, 10 Gbps available at select AWS Direct Connect Partners
- Lead times are often longer than 1 month to establish a new connection
- Dedicated Connections: 1Gbps,10 Gbps and 100 Gbps capacity
- Encryption
- Data in transit is not encrypted but is private
- AWS Direct Connect + VPN provides an IPsec-encrypted private connection
- Good for an extra level of security, but slightly more complex to put in place
- Usecase
- Multiple direct connection can establish for Maximum Resiliency for Critical Workloads
- 2 Direct connect can be used one as a backup, expensive
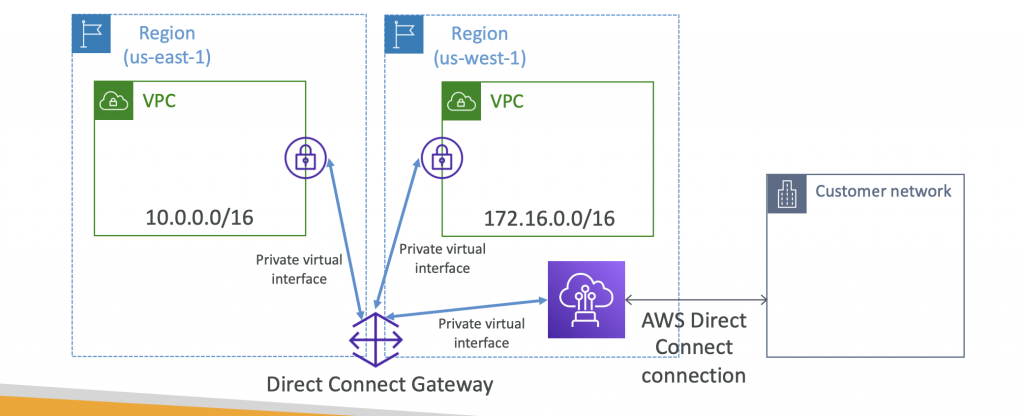
Direct Connect Gateway
If you want to setup a Direct Connect to one or more VPC in many different regions (same account), you must use a Direct Connect Gateway
Network topologies can become complicated
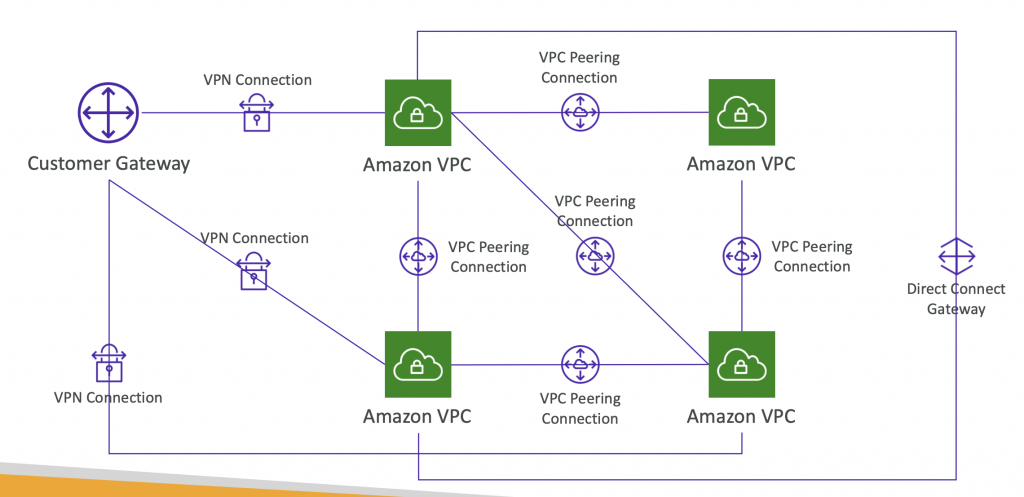
Here we have 4 VPC and 1 Customer Gateway connecting to all VPC, and these VPC are peering with each other. To solve this complexity we have Transit Gateway
Transit Gateway
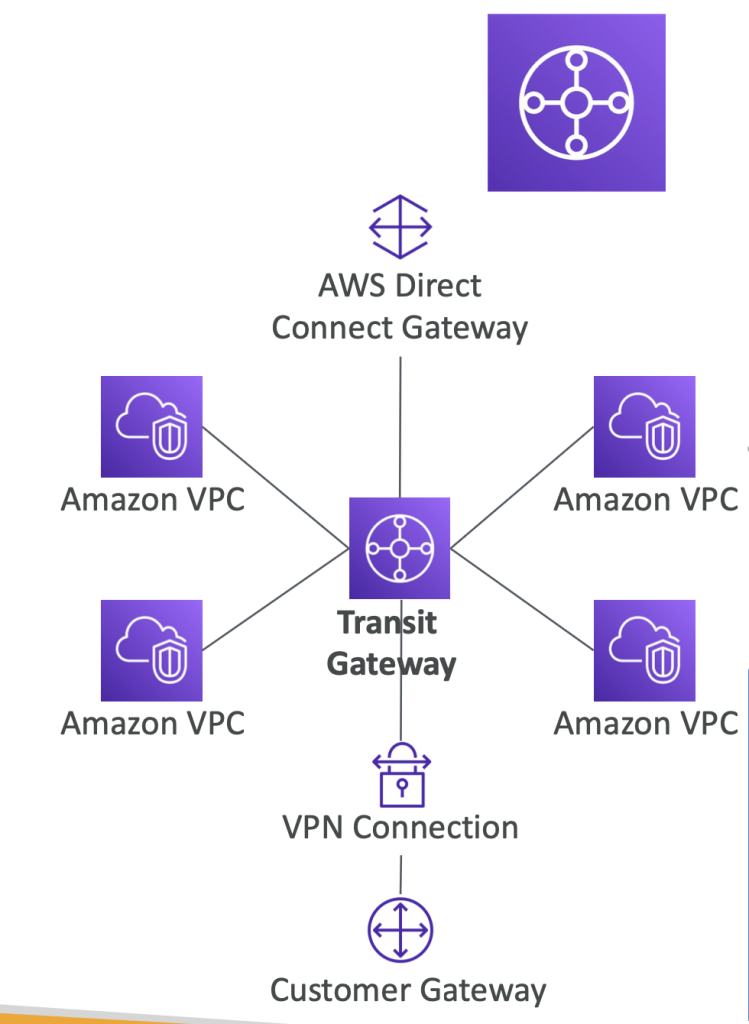
- For having transitive peering between thousands of VPC and on-premises, hub-and-spoke (star) connection
- Regional resource, can work cross-region
- Share cross-account using Resource Access Manager (RAM)
- You can peer Transit Gateways across regions
- Route Tables: limit which VPC can talk with other VPC
- Works with Direct Connect Gateway, VPN connections
- Supports IP Multicast (not supported by any other AWS ser vice)
- We can use multiple Site- to-Site VPN connections to increase the bandwidth of your connection to AWS
VPC – Traffic Mirroring
- Allows you to capture and inspect network traffic in your VPC
- Route the traffic to security appliances that you manage
- Capture the traffic
- From (Source) – ENIs
- To (Targets) – an ENI or a Network Load Balancer
- Capture all packets or capture the packets of your interest (optionally, truncate packets)
- Source and Target can be in the same VPC or different VPCs (VPC Peering)
- Use cases: content inspection, threat monitoring, troubleshooting
Egress-only Internet Gateway
- Used for IPv6 only
- Similar to a NAT Gateway but for IPv6
- Allows instances in your VPC outbound connections over IPv6 while preventing the internet to initiate an IPv6 connection to your instances
- You must update the Route Tables
Networking Costs in AWS
- Free Incoming Traffic from Internet to EC2
- Free for same AZ using private IP
- 0.01$ for Different AZ using private IP
- 0.02$ for Different AZ using public IP
- 0.02$ for Inter Region
- Use Private IP instead of Public IP for good savings and better network performance
- Use same AZ for maximum savings
- Egress traffic: outbound traffic (from AWS to outside) should be minimized
- Try to keep as much internet traffic within AWS to minimize costs
- S3 Data Transfer Pricing
- S3 ingress: free
- S3 to Internet: $0.09 per GB
- S3 Transfer Acceleration:
- Faster transfer times (50 to 500% better)
- Additional cost on top of Data Transfer Pricing: +$0.04 to $0.08 per GB
- S3 to CloudFront: Free
- CloudFront to Internet: $0.085 per GB
- S3 Cross Region Replication: $0.02 per GB
AWS Network Firewall
- Protect your entire Amazon VPC
- From Layer 3 to Layer 7 protection
- Any direction, you can inspect
- VPC to VPC traffic
- Outbound to internet
- Inbound from internet
- To/from Direct Connect & Site-to-Site VPN
- Internally, the AWS Network Firewall uses the AWS Gateway Load Balancer
- Rules can be centrally managed cross- account by AWS Firewall Manager to apply to many VPCs
- Supports 1000s of rules
- IP & port – example: 10,000s of IPs filtering
- Protocol – example: block the SMB protocol for outbound communications
- Stateful domain list rule groups: only allow outbound traffic to *.mycorp.com or third-party software repo
- General pattern matching using regex
- Traffic filtering:Allow,drop,or alert for the traffic that matches the rule
- Active flow inspection to protect against network threats with intrusion- prevention capabilities (like Gateway Load Balancer, but all managed by AWS)
- Send logs of rule matches to Amazon S3, CloudWatch Logs, Kinesis Data Firehose